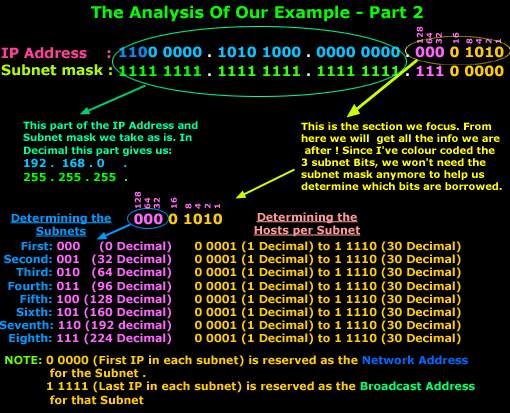
VLANs (Virtual Local Area Networks) and trunking are essential components in modern networking. VLANs enable network administrators to create multiple virtual networks within a single physical network infrastructure. This segmentation improves network performance, enhances security, and simplifies management.
VLANs group devices based on criteria such as department, function, or location, reducing unnecessary broadcast traffic and isolating sensitive data. Trunking is the process of carrying multiple VLAN traffic over a single physical link between switches. This technique allows for efficient data transfer between different VLANs and ensures inter-VLAN communication.
Common trunking protocols include IEEE 802.1Q and ISL (Inter-Switch Link). The implementation of VLANs and trunking optimizes network performance and resource utilization. By dividing the network into smaller, manageable units, VLANs reduce congestion and improve overall efficiency.
Trunking facilitates seamless communication between different network segments, which is particularly important in large enterprise networks with multiple VLANs for various departments or user groups. Effective use of VLANs and trunking allows network administrators to route traffic efficiently and maximize the utilization of network resources. This approach is crucial for maintaining high-performance, secure, and well-organized network environments in modern organizations.
Key Takeaways
- VLANs allow for logical segmentation of a network, improving security and efficiency
- Trunking enables the transmission of multiple VLAN traffic over a single link, reducing network complexity
- QoS prioritizes network traffic to ensure critical applications receive the necessary bandwidth for optimal performance
- VPNs provide a secure way for remote users to access the network, protecting sensitive data from unauthorized access
- NAT allows for the translation of private IP addresses to public ones, conserving IPv4 address space and enhancing security
Implementing Quality of Service (QoS) for Network Optimization
Quality of Service (QoS) is a vital component of network optimization that enables network administrators to prioritize specific types of traffic over others, ensuring that critical applications and services receive the necessary bandwidth and resources.
Improving Application Performance
By implementing QoS policies, organizations can enhance the performance of real-time applications such as voice and video conferencing, while also ensuring that mission-critical data applications receive the necessary resources to operate efficiently. QoS can be implemented at various points in the network, including routers, switches, and firewalls, allowing for granular control over how different types of traffic are handled.
Ensuring Consistent User Experience
Implementing QoS for network optimization is essential for ensuring a consistent user experience and maintaining high levels of productivity within an organization. By prioritizing critical applications and services, organizations can minimize latency and packet loss, ensuring that users have access to the resources they need to perform their jobs effectively. Additionally, QoS can help organizations meet service level agreements (SLAs) by guaranteeing a certain level of performance for specific applications or services.
Optimizing Network Resources
This is particularly important in environments where real-time communication and data transfer are critical to business operations. By implementing QoS effectively, organizations can ensure that their network resources are utilized efficiently and that critical applications receive the necessary priority to operate effectively.
Configuring Virtual Private Networks (VPNs) for Secure Remote Access

In today’s interconnected world, remote access to corporate networks is essential for enabling employees to work from anywhere. However, ensuring the security of remote connections is a top priority for network administrators. This is where Virtual Private Networks (VPNs) come into play.
VPNs provide a secure and encrypted connection between a remote user and the corporate network, allowing employees to access resources and applications as if they were physically present in the office. By configuring VPNs, network administrators can ensure that remote access is secure and that sensitive data is protected from unauthorized access. Furthermore, configuring VPNs for secure remote access is essential for maintaining the integrity of corporate networks and protecting sensitive data from potential security threats.
By encrypting traffic between remote users and the corporate network, VPNs ensure that data remains secure and confidential, even when transmitted over untrusted networks such as the internet. Additionally, VPNs can provide a cost-effective solution for enabling remote access without compromising security, allowing organizations to support a mobile workforce while maintaining strict security standards. By configuring VPNs effectively, network administrators can ensure that remote access is secure and that corporate resources are protected from potential security breaches.
Utilizing Network Address Translation (NAT) for IP Address Management
Network Address Translation (NAT) plays a crucial role in IP address management by allowing multiple devices within a private network to share a single public IP address when accessing resources on the internet. NAT operates by translating private IP addresses to a single public IP address when communicating with external networks, allowing organizations to conserve public IP addresses and improve network security by hiding internal IP addresses from external sources. Additionally, NAT can provide a layer of security by acting as a barrier between internal and external networks, preventing direct access to internal devices from external sources.
Moreover, utilizing NAT for IP address management is essential for conserving public IP addresses and ensuring efficient use of available resources. By allowing multiple devices within a private network to share a single public IP address, NAT helps organizations reduce the need for additional public IP addresses, which can be costly and difficult to obtain. Additionally, NAT can provide an added layer of security by masking internal IP addresses from external sources, reducing the risk of unauthorized access and potential security threats.
By utilizing NAT effectively, organizations can ensure that their IP address resources are managed efficiently and that their network remains secure from external threats.
Implementing Spanning Tree Protocol (STP) for Redundancy and Loop Prevention
Spanning Tree Protocol (STP) is a fundamental networking protocol that plays a crucial role in preventing network loops and ensuring redundancy in switched networks. STP operates by identifying redundant links within a network and blocking those links to prevent the formation of loops, which can lead to broadcast storms and degraded network performance. Additionally, STP allows for the automatic reconfiguration of network paths in the event of link failures, ensuring that traffic can continue to flow through an alternate path without disruption.
Furthermore, implementing Spanning Tree Protocol (STP) for redundancy and loop prevention is essential for maintaining high levels of network availability and reliability. By identifying redundant links and blocking those links to prevent loops, STP helps organizations avoid potential network outages and performance degradation caused by broadcast storms. Additionally, STP allows for the automatic reconfiguration of network paths in the event of link failures, ensuring that traffic can continue to flow through an alternate path without interruption.
By implementing STP effectively, organizations can ensure that their switched networks remain stable and reliable, even in the event of link failures or other network disruptions.
Configuring Access Control Lists (ACLs) for Network Security
Enforcing Security Policies
By configuring ACLs, organizations can enforce security policies that restrict unauthorized access to network resources and protect against potential security threats such as denial-of-service attacks or unauthorized access attempts.
Filtering Traffic
ACLs can also be used to filter traffic within a network, allowing organizations to control the flow of traffic between different segments of the network. This enables organizations to protect sensitive resources and maintain the integrity of their corporate networks.
Ensuring Network Security
By configuring ACLs effectively, organizations can ensure that their network remains secure from potential security threats and unauthorized access attempts. This is essential for protecting sensitive data and maintaining the integrity of corporate networks.
Utilizing Cisco IOS Command Line Interface (CLI) for Advanced Network Configuration
The Cisco IOS Command Line Interface (CLI) is a powerful tool that allows network administrators to configure and manage Cisco networking devices using a text-based interface. The CLI provides access to a wide range of commands that enable administrators to perform advanced network configuration tasks such as device configuration, troubleshooting, and monitoring. By utilizing the Cisco IOS CLI, administrators can gain granular control over their networking devices and ensure that they are operating at peak performance.
Furthermore, utilizing the Cisco IOS Command Line Interface (CLI) for advanced network configuration is essential for gaining a deep understanding of Cisco networking devices and maximizing their capabilities. The CLI provides access to a wide range of commands that enable administrators to configure device settings, troubleshoot issues, and monitor device performance in real-time. Additionally, the CLI allows administrators to perform advanced configuration tasks such as creating VLANs, implementing QoS policies, and configuring VPNs with precision and control.
By utilizing the Cisco IOS CLI effectively, administrators can ensure that their networking devices are configured optimally and operating at peak performance. In conclusion, understanding VLANs and trunking is essential for optimizing network performance and ensuring efficient use of network resources. Implementing Quality of Service (QoS) is crucial for prioritizing critical applications and services over others to improve overall performance.
Configuring Virtual Private Networks (VPNs) is essential for secure remote access while utilizing Network Address Translation (NAT) helps with IP address management. Implementing Spanning Tree Protocol (STP) ensures redundancy and loop prevention while configuring Access Control Lists (ACLs) is crucial for maintaining network security. Lastly, utilizing Cisco IOS Command Line Interface (CLI) is essential for advanced network configuration tasks such as device configuration, troubleshooting, and monitoring.
If you’re interested in learning more about Cisco networking, you may want to check out this article on CCNA training camps. This course can provide you with the skills and knowledge needed to excel in the field of IT networking. Whether you’re looking to advance your career or simply expand your knowledge, this training camp could be a valuable resource for IT professionals.
FAQs
What are advanced Cisco networking techniques?
Advanced Cisco networking techniques refer to the advanced skills and knowledge required to design, implement, and manage complex networking solutions using Cisco networking equipment and technologies.
What are some examples of advanced Cisco networking techniques?
Some examples of advanced Cisco networking techniques include advanced routing and switching configurations, network automation using tools like Ansible or Python, implementing advanced security features such as VPNs and firewalls, and optimizing network performance through Quality of Service (QoS) and traffic engineering.
Why are advanced Cisco networking techniques important for IT professionals?
Advanced Cisco networking techniques are important for IT professionals because they enable them to design and manage complex network infrastructures, troubleshoot and resolve advanced networking issues, and implement advanced security measures to protect the network from cyber threats.
What are the prerequisites for learning advanced Cisco networking techniques?
Prerequisites for learning advanced Cisco networking techniques include a solid understanding of networking fundamentals, experience with Cisco networking equipment and technologies, and a strong foundation in routing and switching concepts.
Where can IT professionals learn advanced Cisco networking techniques?
IT professionals can learn advanced Cisco networking techniques through Cisco’s official training and certification programs, online courses and tutorials, networking forums and communities, and hands-on experience working with Cisco networking equipment in real-world scenarios.